The Domain Name System (DNS) is a vital part of what makes the Internet useable, and the way the entire system works is actually quite fascinating.
All computers and routers that are directly “on” the Internet have unique-in-the-entire-world Internet Protocol (IP) addresses; the allocation of IP addresses in order to ensure this uniqueness is a strictly controlled process, regulated by the government and a whole hierarchy of Internet Service Providers and other businesses. There’s a pretty important reason for this regulation: if any two devices on the gigantic network that is the Internet end up with the same IP address, neither device can communicate. The same is true in any TCP/IP network, even those using the reserved “private” IP addresses commonly deployed in home and business “internal” networks: IP addresses must be unique, or bad stuff happens.
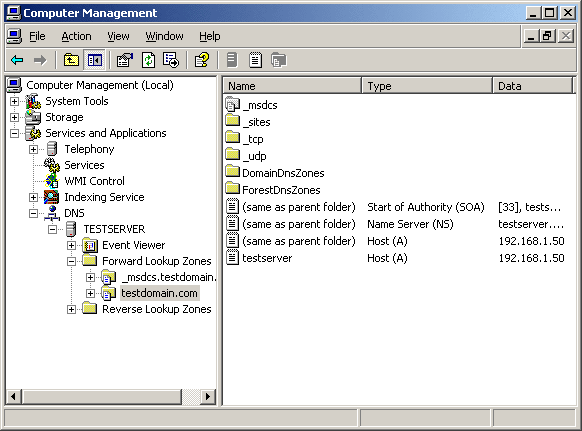
Making this sea of numbers manageable, and destinations memorable, is the job of DNS. DNS assigns unique names which can be associated with these unique IP addresses. This starts with top level domains (.com, .org, etc.) and second level domains (google.com, slashdot.org, …) – again, a strictly regulated trade and for good reason – and there are also “subdomains” for greater levels of specificity. Google.com is a second level domain, for example, whose subdomains include www.google.com, mail.google.com, docs.google.com, and somewhere around a billion others. There is a global network of “nameservers” (including an authoritative set of “root” nameservers at the top) who keep track of this database of information, each record associating a domain name with an IP address. (DNS is actually a bit more complicated and powerful than that, but at its core that’s what DNS does).
When you type a website address into your browser (www.prrcomputers.com, for example), your computer doesn’t initially know what that name means. So after consulting its own “cache” it’s been building from prior web surfing activity, your computer will have been assigned a “primary” DNS server – in other words, the first computer it should ask if it doesn’t know the IP address for www.prrcomputers.com. That primary DNS server might be your own router; if your router doesn’t know, then IT has a primary DNS server it is told to consult – most likely one run by your Internet provider. If that DNS server doesn’t know the answer, IT too has a primary DNS server it is told to ask. And on and on until has an “authoritative” response. The response (an IP address) is then relayed back through all those servers to your computer, who now has enough information to find the computer responsible for the content you’re wanting to browse. All this takes place, typically, in a fraction of a second or at most a few seconds.
Each DNS server, and your local machine, keep a copy of that name+IP record on file in their cache, so if they’re asked again soon they can respond a lot quicker rather than ask up the chain again. The record has an expiration date, and when it expires it is considered “stale,” meaning that the next time the DNS server is asked it’s going to forward that request up the chain of command to get a fresh answer.
This magnificent design is at work every second of every day; it’s the heart of a useful Internet and Web. You can, with complete confidence, visit ebay.com or paypal.com or an address at your bank’s web domain, knowing that this wonderful system is directing you to those places you’re intending to visit. As long as the servers are up and the routers are up and your Internet is up, it works every time.
Except when it doesn’t. What if I told you that there are criminals who are able to covertly redirect your web traffic to servers they control, in order to steal your information? It’s true. DNS can, in fact, be poisoned, and your web browser is none the wiser.
Check back here in a week for Part 2 of this article, I’ll explain how DNS Poisoning works, and some common sense tips that can steer you clear of most of the pitfalls.